Discover all employee-
owned accounts and applications
Discover all employee-
owned accounts and applications
Cloud security products miss 99% of applications and accounts. Discover any web application or SaaS service created with corporate email-based signup.

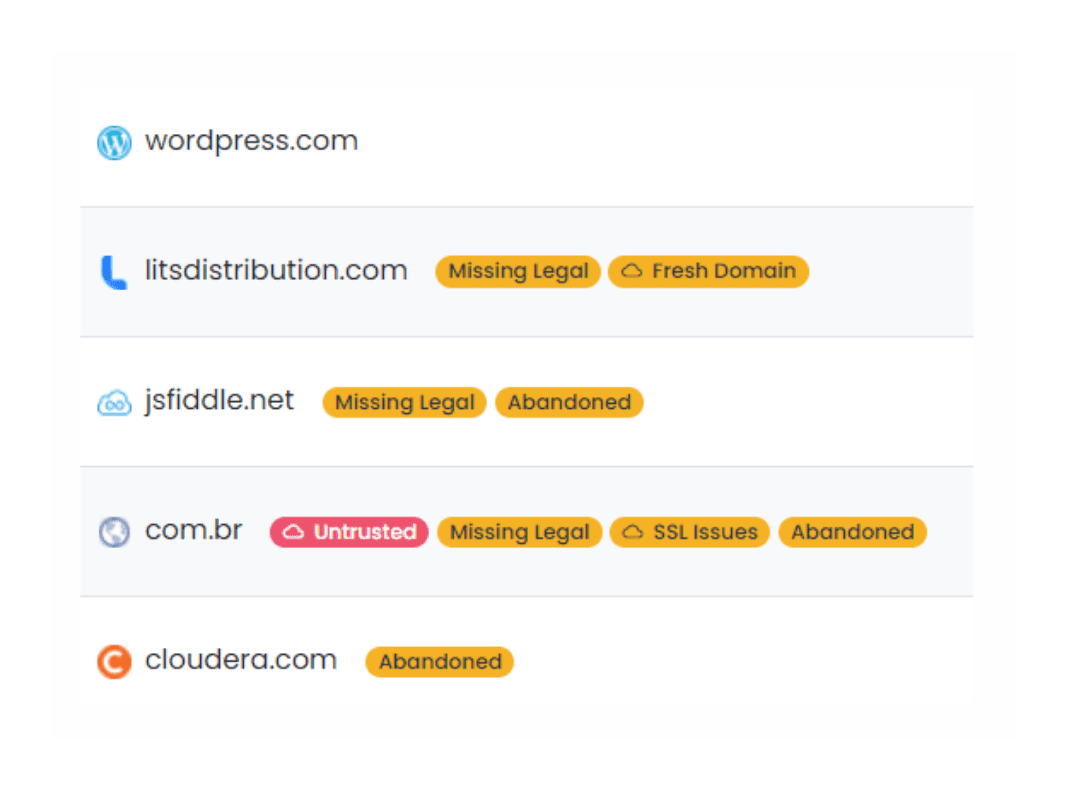
Gain visibility and context for your cloud footprint.
Shadow IT discovery helps reveal emerging trends of cloud usage and legacy or abandoned services that need attention from support, security, or financial aspects.
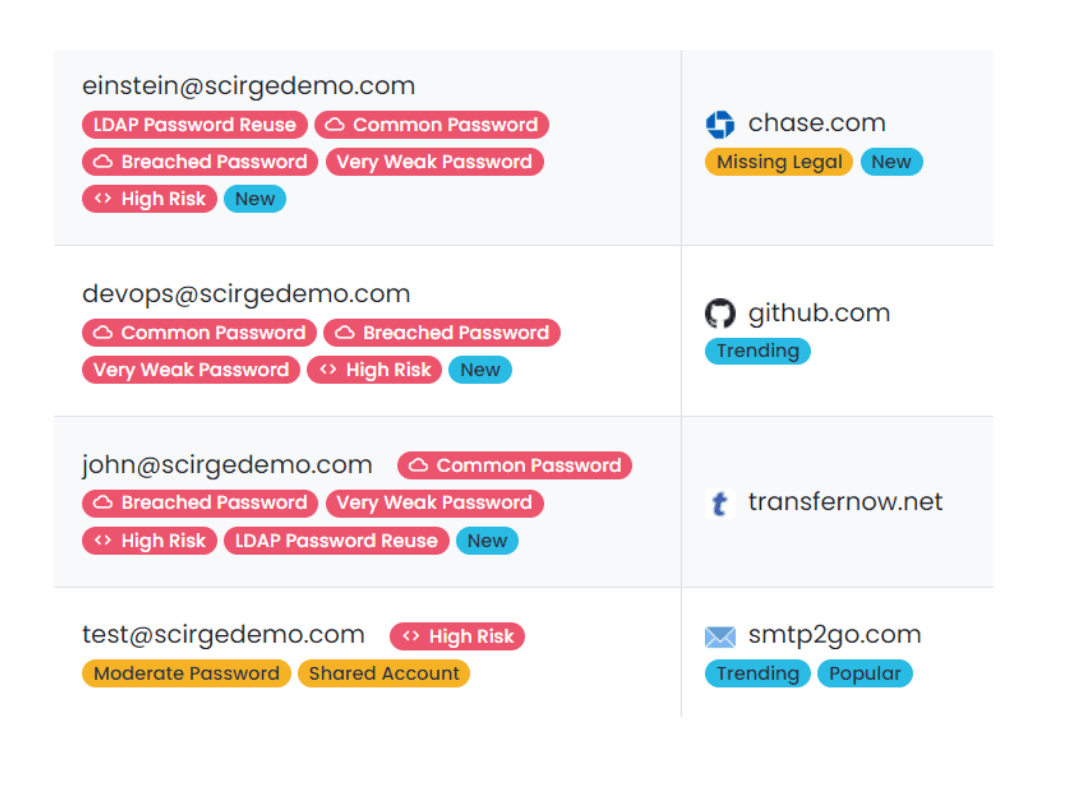
Elevate password hygiene for your AD, LDAP and email-based Accounts
Elevate password hygiene for your AD, LDAP and email-based Accounts
Employee-created passwords are the easiest attack vector. Discover breached, reused, shared, or otherwise insecure accounts without any user interaction or friction.
86% of initial access in breaches are due to stolen credentials.
Fancy cloud security solutions do not address the top initial attack vector at all. Scirge covers all web applications and accounts because it can discover credentials used anywhere online, without relying on a limited number of supported apps or signatures.
Take a step towards cloud visibility.
Shadow IT accounts and web applications create an unmanaged attack surface, operational inefficiencies, and compliance threats. Scirge helps IT and Security decision makers to gain visibility into the digital supply chain, protect unmanaged accounts, reveal identities, and leverage context for compliance and operations.
There are approximately 250,000 new domains registered every single day. Each of them is a potential Shadow IT application.
Fill The Cloud Visibility Gap
Business requirements change faster than IT organizations are able to adapt. Employee-created processes and services in the cloud undermine visibility, efficiency, and security efforts. SSO tax and limited CASB capabilities hinder visibility for most of your digital supply chain.
Simple and Flexible Deployment
Simple and Flexible Deployment
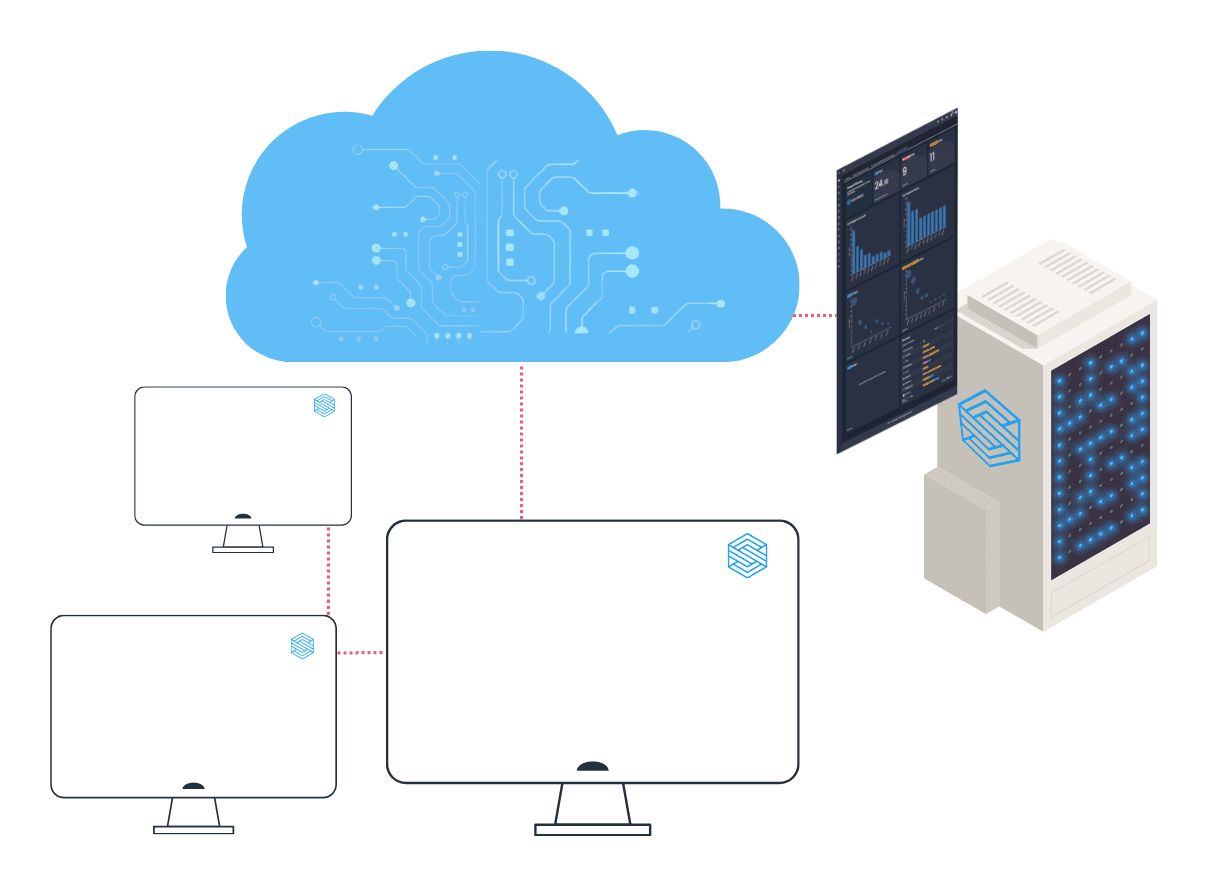
- Scirge has a light endpoint component in the form of a browser extension. Its task is to monitor account and application usage via corporate emails and credentials and perform actions based on centrally-managed policies.
- Management and configuration are available as a native cloud service or as an on-prem appliance. Managed Service Option is also available depending on your region. Horizon Cloud Intelligence services are available in all cases for data enrichment.
- Chrome, Edge, and Firefox browsers are supported on all major endpoint operating systems.